How to Disable TLSv1 Protocol in Apache2
OVERVIEW OF THE ISSUE
I had a client who need to disable TLSv1 from the config of SSL for his website. This is a PCI requirement state that TLSv1 must be disabled by June 30, 2018. This article will explain how can disable TLSv1 from your SSL enabled website running on Apache2 web server.
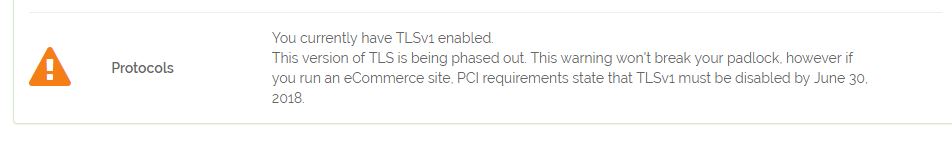
This is the warning you will see when you running a compliance check from online tools. I have run the Test on Why No Padlock?
You currently have TLSv1 enabled.
This version of TLS is being phased out. This warning won’t break your padlock, however if you run an eCommerce site, PCI requirements state that TLSv1 must be disabled by June 30, 2018.
FIX FOR THE ISSUE
First, edit your domain VirtualHost file located in /etc/apache2/sites-available and define SSLProtocal as follows.
SSLProtocol -all +TLSv1.2
This is the sample of full Apache SSL configuration file.
<VirtualHost *:80>
ServerName example.com
Redirect permanent / https://example.com/
</VirtualHost>
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerAdmin webmaster@localhost
ServerName example.comm
DocumentRoot /home/example
ErrorLog ${APACHE_LOG_DIR}/example.com-error.log
CustomLog ${APACHE_LOG_DIR}/example.com-access.log combined
SSLEngine on
SSLProtocol -all +TLSv1.2
SSLCertificateFile /etc/letsencrypt/live/example.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pem
SSLCACertificateFile /etc/letsencrypt/live/example.com/fullchain.pem
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
</VirtualHost>
</IfModule>Finally, restart the Apache2 service, executing the command below.
/etc/init.d/apache2 restart
Now run a Test again and you will see the Protocol warning, no longer shows and the PCI requirement has been passed.
That’s it. ?